A Password Pandemic. How did a COVID-19 password end up online?
The username and password to access the Covid – 19 Information System were publicly available on a health institution’s web page for eight days. This period of time was long enough for the page to be indexed by Google and, although invisible on the web page, it was accessible through a simple search. After discovering the matter on the 17th of April, we immediately informed the competent authorities.
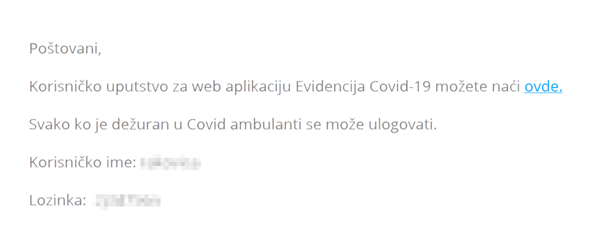
Screenshot of the webpage with login credentials for the Covid – 19 Information System
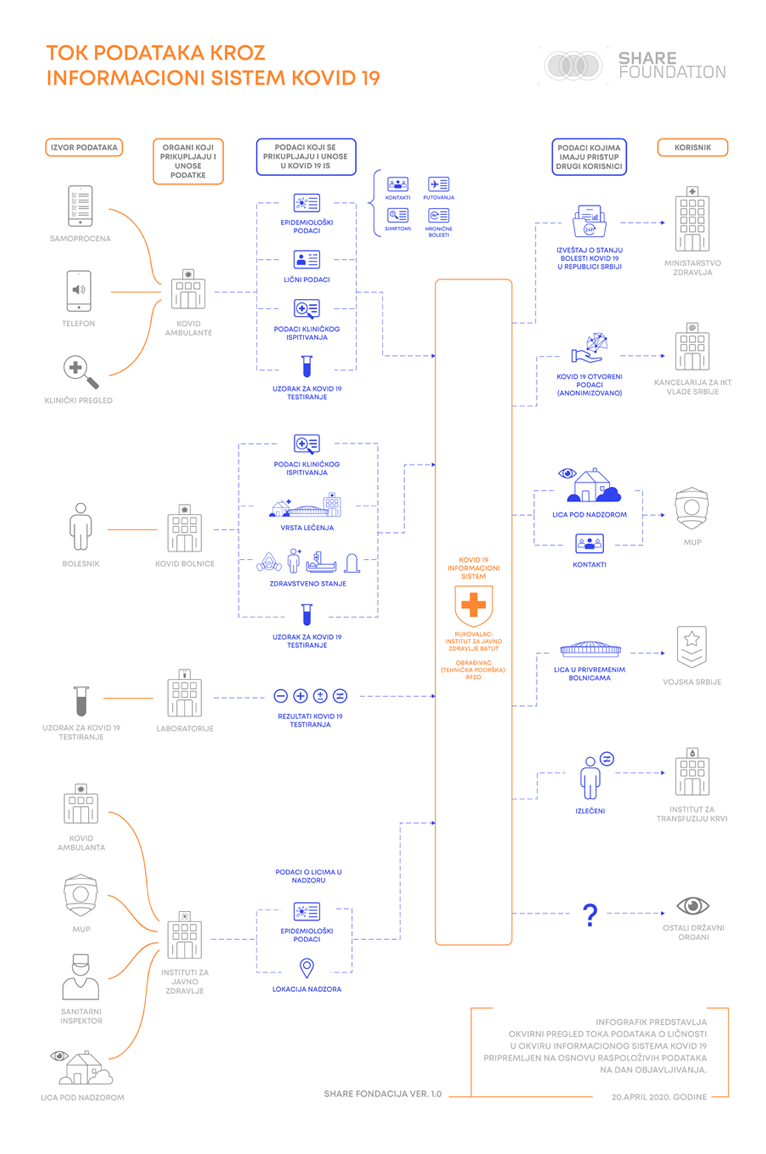
The Covid – 19 Information System is a centralized software for collecting, analyzing and storing data on all persons monitored for the purpose of controlling and suppressing the pandemic in Serbia.
How did we get this data?
Along with the state of emergency, the Government of Serbia introduced numerous measures to tackle the pandemic, which included collecting and processing personal data in the unprecedented circumstances. The Government also informed citizens about these measures by rendering unclear and undetailed conclusions, none of which specified who was supposed to process the citizens’ data and how.
In an effort to understand the data flow and implications on citizens’ rights, we explored the new normative framework through publicly available sources. By searching keywords on Google, we accidentally discovered the page containing access information for the Covid – 19 Information System. The data was published on the 9th of April.
In addition, we also managed to obtain manuals with instructions for navigating the centralised system webpage.
Which data was at risk?
As per Government’s Conclusion on establishing the Covid – 19 Information System, a significant number of health institutions is required to use the mentioned software to keep records on cured, deceased and tested persons (whether positive or negative), as well as on persons currently being treated, in self-isolation or put in temporary hospitals, including their location data. This system also contains data on persons who are possible disease-carriers due to their contact with other infected persons. The institutions are required to provide daily data updates, as it’s the basis of the diurnal 15 o’clock report read.
While attempting to clarify how our data is being stored, we could not have imagined that we would discover the access password and thus be able to enter the system – just as anyone else who may have found this webpage. It was immediately clear to us that the most sensitive citizens’ data were endangered and that the crucially important integrity of the system cannot be guaranteed in the fight against the pandemic.
We did not log into the system, which would anyway record such an attempt. Instead, we reported the case to competent authorities: the Commissioner for Information of Public Importance and Personal Data Protection, the National CERT and the Ministry of Trade, Tourism and Telecommunications. Being aware of the risk of misuse arising with the accessibility of citizens’ sensitive data, we have decided to notify the public of the incident only after making sure that the authorities had prevented unauthorized access to the system.
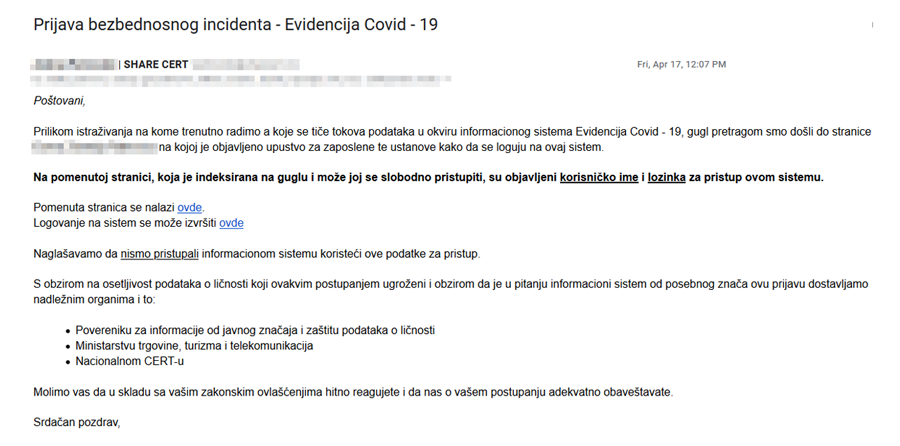
Report of the breach sent to competent authorities by email
How did the competent bodies react?
Less than an hour following our report, we were informed that the initial steps were taken as a response to the incident, makings sure that the web page containing the username and the password is no longer publicly available.
Given the scope of the case, we may expect further action from the competent bodies. The Commissioner has the authority to initiate monitoring in line with the Law on Personal Data Protection, the competent ministry is in charge of the inspection monitoring in line with the Law on Information Security, whereas the National CERT has the obligation to provide advice and recommendations in case of an incident.
Who’s to blame?
Aware of the pressure put on health services at the peak of the pandemic, we agreed that, for now, it would be appropriate not to publish the information on the specific health institution in which the incident took place. On the other hand, there is no doubt that the scale of this incident demands that the responsibility for its occurrence is properly determined.
The national legislative framework provides various mechanisms to prevent these kinds of situations, but the occurrences in practice are often far from the prescribed standards. Although they handle particularly sensitive data, health workers are often unaware of all possible risks present in the digital era. Health institutions are required to appoint a data protection officer, but due to limited resources, persons with insufficient expertise and unrelated primary job concerns are usually appointed to this position. In this specific case, the data protection officer may have been a person who takes care of corona-infected persons on a daily basis.
As today’s data protection demands the involvement of an IT expert, this requirement causes an additional burden to the public health institutions’ budget. Sometimes this means that the same person deals with all technical issues within an institution, while being paid far less than their private sector counterparts and without the opportunity to build further information security expertise.
Covid – 19 Information System established by the Government represents a key point in a complex architecture for collecting and processing all defined data. Data collection occurs through different channels, while a single health institution is only a one system entrance point. In such a system, it is rather difficult to implement protection measures at entrance point level, meaning they should be defined at the central level as it would significantly lower the risk of incidents. Based on this case, we have concluded that only one user account was created for each of the health institutions, which does not enable determining individual responsibility for the system misuse.
What should have been done?
Without doubt, this is an ICT system of a special importance within which special categories of personal data are being processed. As such, it implies the necessity to undertake all measures stipulated by the Law on Information Security and the Law on Personal Data Protection in phases of its development and implementation. SHARE Foundation explored these measures to a great detail in its Guidebook on Personal Data Protection and Guidebook on ICT Systems of Special Importance.
By any means, it is necessary to fully implement privacy by design and security by design principles, which entail the following regarding the access to a system:
- Every system user has their own access account
- Every system user has the authorisation to process only the data necessary for their line of work
- Access passwords are not published via an open network
- A standard on password complexity is put in place
- The number of incorrect password entries is limited
Our accidental discovery on Google revealed a breach of security and data protection standards within the health system. The state of emergency instituted due to pandemic cannot serve as an excuse for a job poorly done, nor can it serve as an obstacle for conducting an immediate detailed analyses of compliance of Covid – 19 Information System with security standards.
Read more:
- Digital rights in the Balkans: endangered privacy of patients
- Limitation of rights and freedoms during a public health crisis
- The day after the pandemic: are we going towards a surveillance dystopia
- Privatisation Agency: a unique case
Attachment: Data flow in the Covid – 19 Information System